- Topic1/3
24k Popularity
39k Popularity
4k Popularity
551 Popularity
710 Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is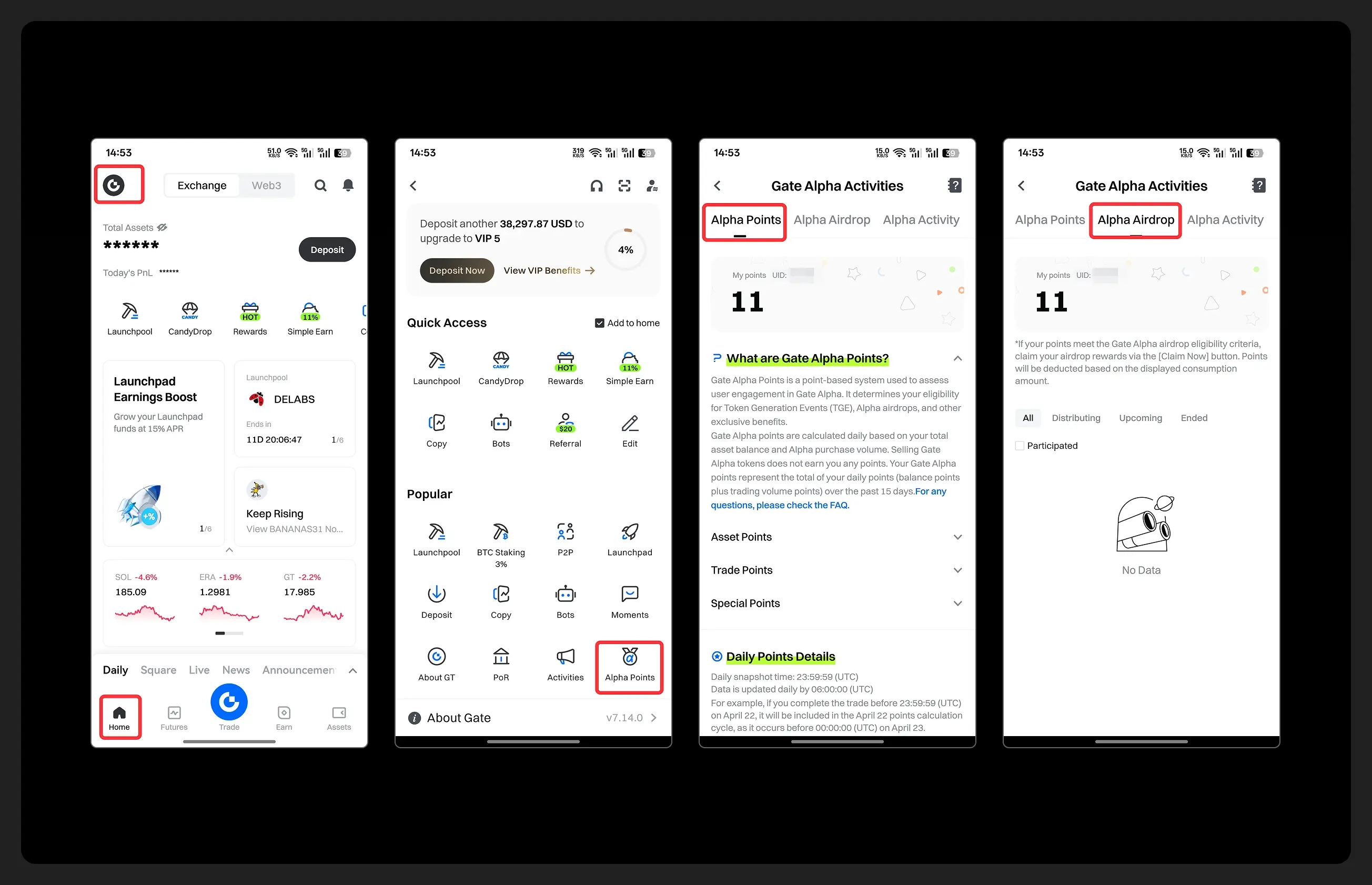
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
Rust Smart Contracts Security Advanced: Permission Control and Access Management Practices
Rust Smart Contracts Development Diary (7) Contract Security and Permission Control
This article will introduce permission control in Rust smart contracts from two perspectives:
1. Contract Function Visibility
Visibility control of contract functions is crucial for protecting key functionalities. For example, in the security incident of Bancor Network exchange in June 2020, the risk to user assets arose because a critical transfer function was mistakenly set to public.
In Rust smart contracts, there are the following types of function visibility:
Additionally, defining a function in an impl block that is not modified by #[near_bindgen] can also make it an internal function.
For the callback function, it must be set to public but also ensure that it can only be called by the contract itself. This functionality can be achieved using the #[private] macro.
It should be noted that the default visibility in Rust is private, which is different from the default public in some versions of Solidity. The exceptions are that items in pub trait and pub enum are public by default.
2. Access Control of Privileged Functions
In addition to function visibility, a whitelist mechanism needs to be established to control access to privileged functions. Similar to the onlyOwner modifier in Solidity, an Ownable trait can be implemented:
rust pub trait Ownable { fn assert_owner(&self) { assert_eq!(env::predecessor_account_id(), self.get_owner()); } AccountId; fn set_owner(&mut self, owner: AccountId); }
This trait can restrict only the owner from calling certain privileged functions. Based on this principle, more complex whitelists can be set up to achieve fine-grained access control.
3. Other Access Control Methods
Other access control methods such as contract invocation timing control, multi-signature invocation mechanism, and DAO governance can also be considered. These will be detailed in subsequent articles.